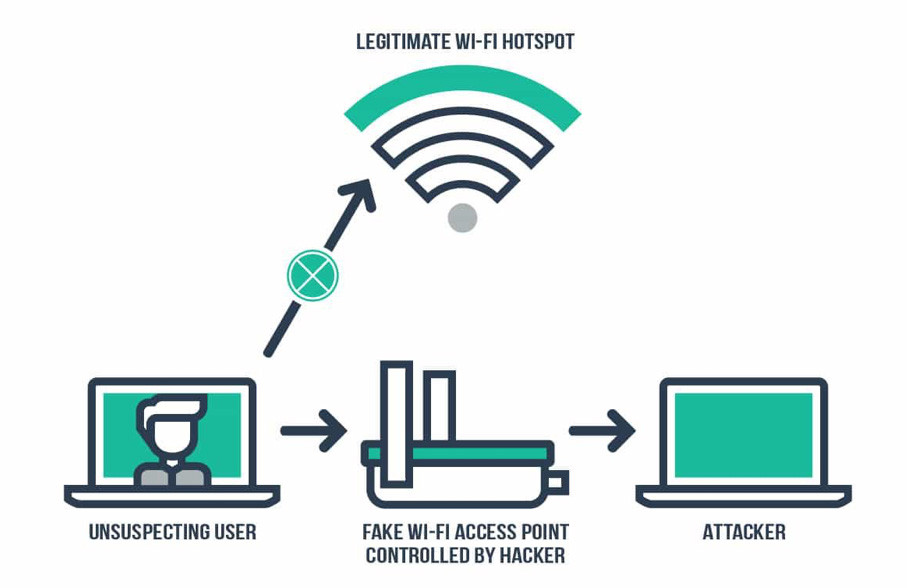
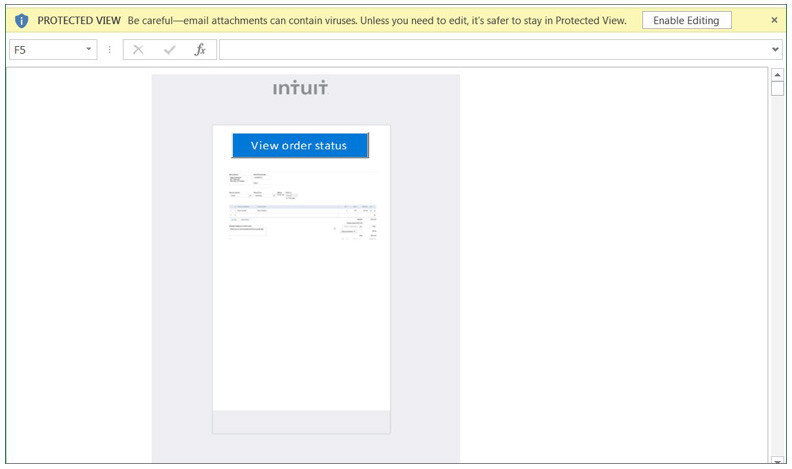
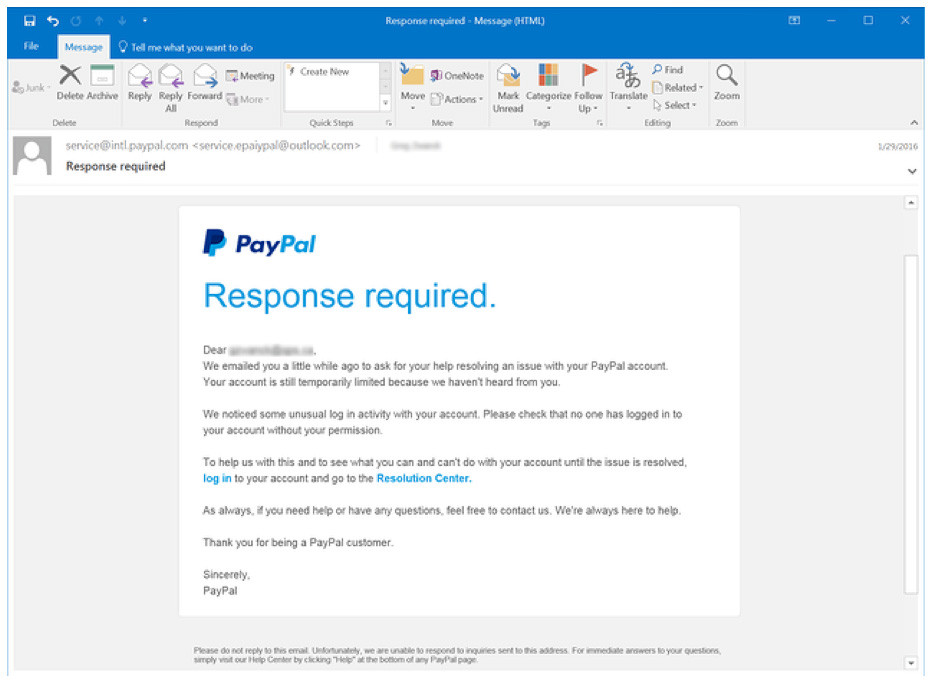
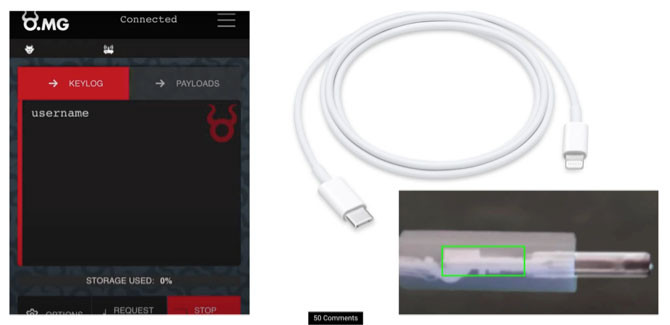
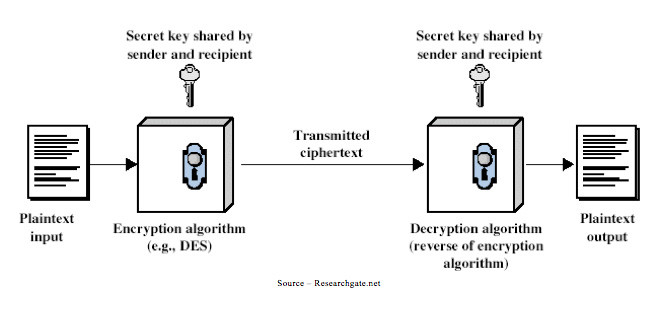
Cryptocurrency is not hack proof as your money is stored in digital wallets that are a much easier target than blockchain technology. The Bitcoin goldrush has meant that many new to the cryptocurrency scene are investing without fully understanding how the currencies work-and many in the industry do not care. This has left the door open for cybercr...

To guide, inspire and prepare Wyomingites and their fellow Americans to act against existential threats to their liberties and to Western Civilization from radical revolutionaries and Emperors who have no clothes.